Browser hijackers can be downright annoying, with the malicious software spamming you with ads, tracking your browsing activity, and hijacking your search engine. Worse still, some browser hijackers can pave the way for more malware to be installed on your device. Some common examples include:
- Ask Toolbar
- CoolWebSearch
- Coupon Server
- GoSave
Fortunately, you can remove malware, including browser hijackers, from your system, either by uninstalling them or by using good antivirus software.
To protect yourself from browser hijackers and other forms of malware, it’s always wise to use a VPN. NordVPN is an excellent VPN that comes with Threat Protection built-in, which protects your computer in real-time from harmful threats.
For more information on how to remove browser hijackers, check out our full article below.
New types of malware are detected almost regularly. In 2020, SonicWall recognized more than 268,000 different types of malware variants. That number’s likely to have gone up in 2022. Browser hijackers are just one of the many new types of malware used today, and worse still, many of them pass off as genuine software.
In this article, we’ll answer the titular question: what is a browser hijacker and how do I remove one? We’ll also cover examples of the most common browser hijackers so that you know what to look for and how to keep your devices secure.
What Is a Browser Hijacker?
Browser hijackers are a type of malware (malicious software) that can quite literally hijack your internet browser. Once infected, hijackers forcibly change your web browser’s settings without your approval.
Some browser hijackers are more annoying than dangerous, generating tedious pop-up ads that provide marketing income for the creator. These hijackers, which are a form of adware, can be irritating, as they make it difficult to browse content without interruptions.
However, others are far more malicious and can capture data entered into the browser through a process known as keylogging. Some can even introduce malware into your computer.
4 Common Browser Hijackers
To help you identify browser hijackers and avoid installing one by mistake, we’ve covered some of the most common types below. If you spot any of these on your computer while installing new software or browsing the web, check out our guide on how to remove browser hijackers further down in this article. Typically, a browser tracker will fall into one of three categories:

- Adware: Adware is designed to spam you with advertisements in the hope you’ll part with your money. By clicking on adware pop-ups, you’re putting money directly into the pockets of the people who create these frustrating tools. And aside from being irritating, they consume lots of resources, slowing down your computer.
- Trackers: Trackers do exactly what they say on the tin; they track your activity online, keeping logs of everything you do online. This includes keeping detailed records of your browsing history, IP address, search history, and more. They use this information to send targeted advertisements to unsuspecting individuals. Your details could also be resold to third parties.
- Malware: The most malicious browser hijackers can install malware onto your computer. This could lead to worse problems such as identity theft or even ransomware that locks you out.
To give you an idea of what you’re looking out for, we’ve detailed some of the more common browser hijackers below.
1. Ask Toolbar

When you install new software onto your computer, you might notice the installation wizard asking if you’d also like to install the Ask Toolbar. If you agree, it’ll automatically change your default search engine and your homepage. This toolbar is an example of a browser hijacker that hides in plain sight.
You may remember an online company called Ask Jeeves from the early days of the internet; this is the same company, rebranded. The toolbar is well-known for filling your browser with adware, failing to return comprehensive search results like Google would, or simply redirecting your searches to sponsored websites.
2. CoolWebSearch
This hijacker is a type of spyware that’s capable of taking over your search engine, and it can infect any popular browser, including Chrome and Firefox. It’ll redirect your search engines so that they’re forced to use the CoolWebSearch engine, which gathers marketing revenue and logs your search activity.
You could even find your internet browser’s favorites and browsing history filled with adult content and sponsored websites. It uses various techniques to prevent removal, especially since it’s bundled with other programs that you might accidentally install.![]()
3. Coupon Server
This is another type of adware, and as the name suggests, spams you with pop-up windows that offer money-saving coupons and other shopping links. Unfortunately, these links redirect you to even more adware and spyware. You may also be forcibly directed to the Coupon Server homepage, which has been camouflaged to look like a search engine.
4. GoSave
Like Coupon Server, GoSave promises discounts for online shopping, but they’re obviously false. Instead, you’ll be hounded by online advertisements that spam your search queries and other activities online. What’s more, if you follow any of the links, there’s a risk of a serious malware infection too. This hijacker can also capture information including your IP address, cookies, and other browsing data.
Browser hijackers on Mac
Since Apple’s operating system is quite different from Windows or Android, the browser hijackers that target Macs are a little different. If you’re using a Mac, you should also be on the lookout for the following malicious toolbars:
- Search Baron
- Safe Finder
- Trovi
- Weknow.ac
- Bing Redirect
Bear in mind that you might want to do a review of your Mac’s security settings, as, for example, Mac’s firewall is typically disabled by default on new machines. We’ve written an article on how to change your Mac’s privacy settings.
7 Tips To Protect Your Browser From Hijackers
While you can’t guarantee that you’ll never unwittingly download a browse hijacker, there are some good cyber hygiene habits you can follow to avoid falling victim to unwanted browser malware. Below, we’ve detailed some tips that will help you to prevent browser hijacking and ensure that your web browser remains secure:
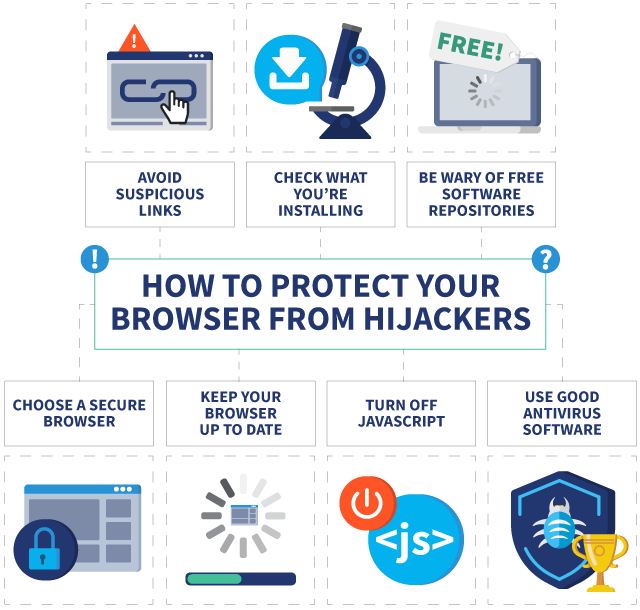
1. Avoid links, attachments, and downloads from suspicious sources
When it comes to cybersecurity, this is a general rule that you should follow. Avoid downloading software from unknown sources. Also, start using a private search engine.
2. Always check what you’re installing
As we’ve mentioned above, some software installation wizards will offer you browser toolbars and extensions. Make sure you read the instructions on-screen and deselect any checkboxes that are automatically ticked for you.
3. Be wary of free software repositories
Be careful when downloading new software from the web. While you may find a legitimate download for the software you want, it’s not uncommon for browser hijackers to be packaged alongside software.
4. Choose a secure browser
Ideally, you should be using well-known and trusted internet browsers, such as Google Chrome, Firefox, Edge, or Safari. However, not all of these browsers are perfect in terms of privacy and security. It’s best if you use dedicated browsers for privacy.
5. Keep your browser up to date
In addition to running regular updates, make sure that you keep your internet browser up to date. Hackers continually discover new exploits and vulnerabilities, so it’s essential to update your browser.
6. Turn off JavaScript
JavaScript is used by many programs to deliver interactive web content, but it can also be abused by malicious actors. By disabling Javascript, you can reduce the number of risks that you’re exposed to when browsing the internet, though it will affect site functionality.
7. Use antivirus software and a VPN
The best antivirus software offers increased protection against online threats beyond simple device scanning, including extensions that detect malware in real-time.
Of course, even when you use cybersecurity software and follow all of the cyber hygiene habits outlined above, there’s still a risk of infections. Below, we’ll outline the warning signs that tell if your browser has been hijacked.

One of the best ways to protect your computer from browser hijackers is to use a VPN with cyber security features built-in. NordVPN is an excellent VPN that prioritizes user security. It’s got an extensive server network and uses the latest security technologies.
More importantly, NordVPN offers Threat Protection, which stops you from downloading malicious software. It also prevents you from landing on harmful sites and blocks any intrusive ads or trackers on the spot.
- Excellent protection and a large network of servers
- Nice and pleasing application
- No logs
How To Tell if Your Browser Has Been Hijacked
Fortunately, most browser hijackers will show one or more telltale signs that they’ve made their way onto your computer. It might be time to understand how to remove a browser hijacker if you notice one or more of the following signs:

- Webpages loading slower than you’re used to
- Constant pop-up advertisements that follow you from site to site
- Your default search engine, for example, Google, has been replaced by something else
- New icons or toolbars appearing in your browser
However, bear in mind that not all browser hijackers will signpost their arrival on your device. If a browser hijacker infects your internet browser but doesn’t give away its presence, it’s possible that the malware may spy on your internet activities.
In this case, it could be gathering data, installing tracking malware on your device, or recording information that you input into websites, such as keystrokes. Keyloggers are a serious problem, and often hide their presence. In either case, it’s time to remove the browser hijacker from your computer.
How To Remove a Browser Hijacker
The good news is that most browser hijackers can be simply uninstalled from your device without much effort. Below, we’ve covered the steps to follow to remove browser hijackers from popular browsers.
How to remove a browser hijacker from Google Chrome
 Start by opening the Chrome browser on your computer.
Start by opening the Chrome browser on your computer.- Click on the menu (3 small dots) and then Settings. On Mac, you’ll have to choose “Chrome” and then “Preferences” at the top of your screen while the browser is open.
- Scroll down a little, then select “Advanced.”
- Select “Reset settings” and then “Restore settings to their original defaults.”
- Finally, click on “Reset settings” one final time to confirm. This will clear your cookies and remove any browser hijackers, though bear in mind that it’ll remove any of your legitimate Chrome extensions too.
How to remove a browser hijacker from Firefox
 Start by opening Mozilla Firefox on your computer.
Start by opening Mozilla Firefox on your computer.- Open the menu (3 small lines) and then choose “Help.” On Mac, you’ll need to click “Firefox” and then “Preferences.”
- Now, choose “More troubleshooting information.”
- Finally, select “Refresh Firefox” to reset your browser to its original settings and remove any unwanted extensions or trackers.
How to remove a browser hijacker from Microsoft Edge
 Start by opening Edge on your device.
Start by opening Edge on your device.- Locate “Settings” within the three-dot menu, similar to Chrome. On Mac, again, you’ll click on “Edge” and then “Preferences” first.
- Click on “Reset settings” in the menu on the left-hand side.
- Finally, click on “Restore settings to their default values” to reset your browser to factory defaults.
How to remove a browser hijacker from Safari
 Click on “Safari” at the top of your screen while Safari is open.
Click on “Safari” at the top of your screen while Safari is open.- Select “Preferences” next. As a side note, in the “Privacy” menu, you can disable Javascript if you like.
- Click on “Extensions” and look for any unwanted browser hijackers or toolbars that are visible here.

- Choose to “Uninstall” any unwanted extensions after selecting them to remove them from Safari.
However, bear in mind that this may not get all browser hijackers if you’re dealing with some of the sneakier, more malicious hijackers. In this case, follow the steps below to be sure:
- Click on the small Apple icon at the top of your screen.
- Select “About This Mac” (which may be “Overview” on some devices) and then choose “System Report.”
- Under the “Software” parent menu, select “Applications.”

It’s always wise to be vigilant. We’ve given you the names of some of the most common browser hijackers. However, pay attention to any software you don’t recognize and verify its purpose using Google.
If in doubt, drop us a comment below, and we can tell you whether you have malware that needs to be removed!
Final Thoughts
While browser hijackers can pass themselves off as innocuous tools that are offered alongside legitimate software, you should never install unknown software onto your device. The consequences could range from minor annoyances to full-blown identity theft, and you could be paving the way for other malware infections.
Instead, follow our advice on how to remove a browser hijacker if you start noticing any of the common signs that we’ve outlined above. You should also familiarize yourself with good cyber hygiene habits, in addition to ensuring that you’re using a combination of the best cybersecurity tools to keep yourself safe online.
Got questions about browser hijacking and how to remove browser hijackers from your device? Check out our frequently asked questions below!
Browser hijacking occurs when malicious software infects your internet browser to change its behavior. The browser hijacker may modify your internet browser’s settings, changing your homepage or search engine. It may redirect your search queries or attempts to visit a website so that you’re forced onto malicious websites instead.
Broadly speaking, there are two ways to prevent browser hijacking. The first involves protecting your devices with the best cybersecurity tools, including antivirus software and a VPN. However, the best way to avoid browser hijacking is through good cyber hygiene habits:
- Don’t click on suspicious links or download unknown attachments or software.
- Choose a secure browser; you can also use CyberGhost Private Browser for added protection.
- Keep your browser up to date with the latest security and software updates.
- Be wary of free software repositories
- Always deselect the checkboxes in installation wizards that promise free browsing tools
There are some telltale signs that your browser may have been hijacked. You may need to follow our step-by-step guides on how to remove a browser hijacker from the most popular internet browsers if you notice any of these signs:
- Webpages start loading much more slowly than usual
- Your device is affected by constant pop-up advertisements
- Your homepage or default search engine has been changed to something you don’t recognize
- There are new icons or bars at the top of your internet browser
Most browser hijackers aren’t the best at disguising their identity. For many of the common browser hijackers, you can simply go into your internet browser’s settings and “restore factory settings.” We’ve got a step-by-step guide for removing browser hijackers that you can check out.


